Data Consumers
Buy and use data
you can actually trust.
Data Consumers
Buy and use data
you can actually trust.
Who Are Data Consumers?
Today, as a data consumer, you rely on providers to assure you that data was collected with consent. If they are wrong, the liability falls on you.
LayerD changes this by embedding a Proof of Consent layer directly into the data pipeline.

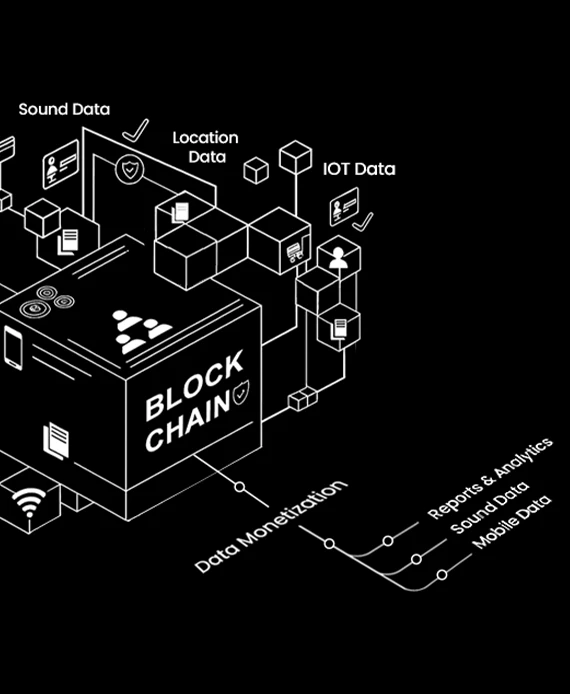
How It Works
Consent Validation Layer
Every dataset links to an immutable Proof of Consent record showing if the user opted in, opted out, or revoked permission.
Direct Proof, Not Promises
No more blind trust. You verify consent status at the protocol level, instantly, transparently, and without intermediaries.
Seamless Pipeline Integration
LayerD connects with your existing ingestion and analytics workflows via SDKs and APIs, so you can enforce compliance without rebuilding infrastructure.
Monetize with Confidence
Verified-consent datasets command higher value. By consuming only compliant data, you minimize regulatory risk and maximize brand-safe monetization.
Use Cases

Advertisers & DSPs
Run campaigns on verifiably opted-in audiences and prove compliance to brand partners.

AI & ML Companies
Train models on tamper-proof datasets with cryptographic consent, reducing bias, liability, and compliance risk.
• Use only verified, consented data
• Lower compliance exposure
• Build trustworthy AI models

Analytics Platform
Deliver insights with full visibility into data provenance, ensuring results that stakeholders can trust.
• Ensure compliance-ready reports
• Trace data to source
• Strengthen stakeholder confidence
The Challenge Today
Data consumers rely on claims from upstream providers, not proof from users.
Consent signals are fragmented, unverifiable, and risky, creating blind spots that lead to bias, breaches, and costly penalties.


FAQs for Data Consumers
Simply check your dataset or device IDs through LayerD. The system provides real-time consent status based on blockchain-anchored proofs, showing whether it is active, revoked, or missing - all cryptographically validated without relying on upstream claims.
No. Unlike providers, consumers don’t integrate LayerD SDKs by default. Verification is done through our platform, APIs, or custom integrations if required.
Every dataset you use is tied to a verifiable Proof of Consent. This protects your business from regulatory fines, reputational damage, and the costs of manual audits.
Yes. Verified-consent datasets hold higher market value. Using LayerD means you’re working with premium, brand-safe data that advertisers and stakeholders trust.
LayerD’s reflects consent changes in real time, allowing you to verify the latest status before processing or reusing any dataset. Notification features for automated updates are coming soon.